There is no denial that security of data and other information is critical in the backdrop of our journey as citizens as well as a country towards a Digital Nation. The recent notification from the Ministry of Electronics and Information Technology, Government of India, to various handset makers is a welcome step in this direction, as measures from government not only increase awareness and sensitize users, but also reassures ordinary users of a service or product that the scene is not unattended.
However, at the same time, CMR believes that while a lot of security measures like encryption of data, fingerprint sensors, etc. have already been incorporated in devices, particularly of mid to premium price handsets, emphasis must also put on the value chain responsible for software aspects like OS, UIs and apps within the purview and hold an extended audit in the same context.
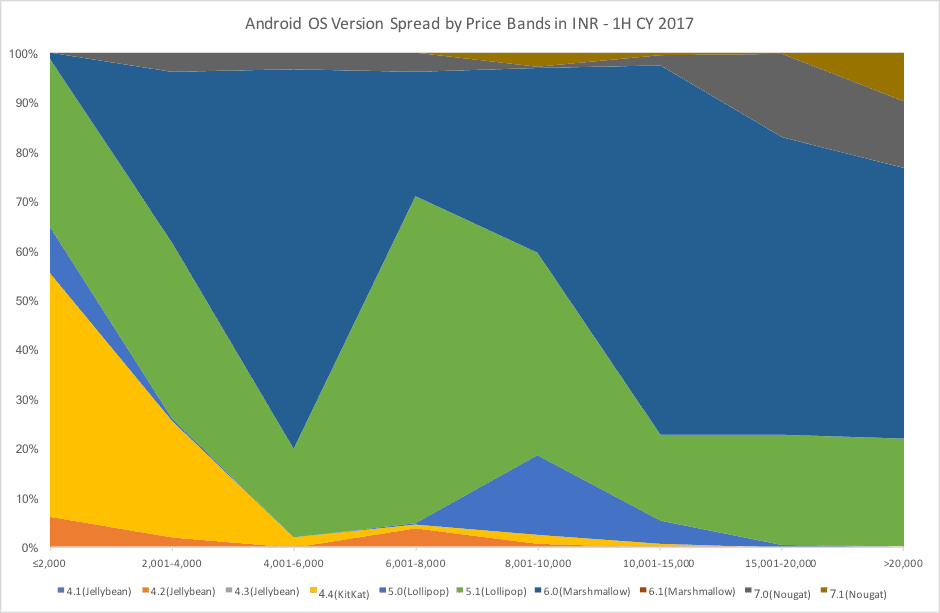
At present, over 90% of Smartphones run on Google Android OS and with each upgrade of the OS, Google has hardened the security of the devices. However, problem is that handset makers do not upgrade the versions on existing devices in use as a routine. Also, there is a strong correlation between the latest OS version and the price of a Smartphone. Over 22% of the shipments for 1H CY 2017 of Smartphones were priced up to Rs 6,000 and the above chart depicts the OS Version spread skewed towards earlier versions of Android. This keeps the typically less aware user profile purchasing entry level Smartphones deprived of the security improvements that Google brings at the OS level.
CMR believes that while handset manufacturers can be mandated by the government to ensure that OS upgrades, as rolled out by Google, are instantly pushed across to users across price segments, especially the security patches. Beyond this, handset vendors can also be audited for the information they collect via UIs that are installed on the handsets.
The security vulnerability needs to be looked from a holistic viewpoint. For ensuring a secure environment of privacy and data for a user, along with hardware the software aspects especially apps also need to be taken in to account. Apps go through predefined checks of Google after which they are published on the Play Store. Once, available on the Play Store, handset vendors cannot control what is to be enabled or not, on to a device.
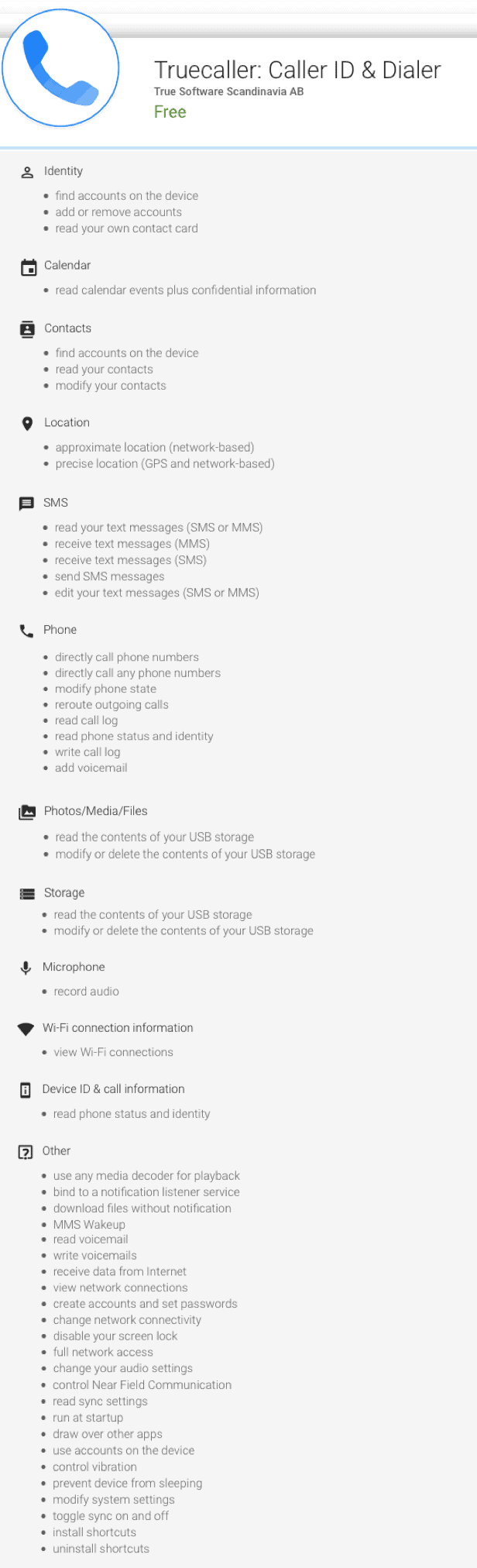
Awareness among users also has a critical role to play. For instance, one of the most popular app used in India True Caller, which majority of us see as an app offering Caller ID facility, has too many permissions that it asks for while someone installs the app. Very few users must be going through such details and ultimately would be passing on information which they would never be thinking of. For instance, among other permissions, True Caller also seeks permission for ‘recording audio’ (See list of permissions that True Caller invokes while someone installs the apps). With the general usage that any ordinary user understands of an app like True Caller, why would it be requiring recording of audio permission? Looking at the list of permissions, an app like True Caller could be more detrimental than what the information accessed and captured by a device manufacturer could harm.
True Caller is still an app of repute. We have so many publishers on Google Play and several unknown or lesser known publishers who could be playing with the data they are able to access and gaining little through the ‘face value’ purpose of the app. The government must impress upon the OS vendors to have more clarity on the purpose of accessing such capabilities of a device for which permissions are sought upon installation.
Conclusion
To have a holistic approach towards this ever-increasing threat of data theft especially on Smart and Connected devices, it is imperative to audit the entire value chain and create self-checking measures in the system that would see regulations more of enabling than impeding. The categorization of origin of a brand viz-a-viz security vulnerability may not be a constructive approach towards resolution of the issue and should be seen from various other perspectives as well, as highlighted in this note.













